/ 04. Educate and Empower Your Employees
Your employees are your first line of defense and your biggest risk.
Regular training sessions can turn potential security risks into your strongest allies. Teach them to recognize threats and avoid risky behavior. After all, the smartest people can sometimes make the dumbest mistakes when they're not aware of the risks.
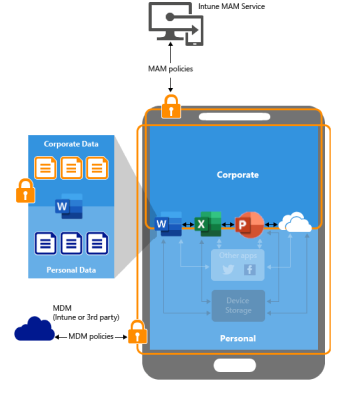
/ 05. Separate Corporate and Personal Data
Even with BYOD and company-issued devices, corporate and personal data must be kept separate.
Implement technology to create isolated environments for work-related data and applications. By maintaining strict boundaries, you minimize the risk of data breaches and compromise for both personal and corporate data.